Secure IoT: Connect Devices Via VPC & Raspberry Pi
In an era defined by relentless technological advancement, is it possible to safeguard the vital flow of information from remote Internet of Things (IoT) devices? The answer, unequivocally, is yes. The marriage of a Virtual Private Cloud (VPC) and a humble Raspberry Pi has emerged as a cornerstone skill for developers and tech enthusiasts alike, addressing the critical need for secure communication and data transfer in our increasingly connected world. Securing these devices is not just a consideration, it's a necessity. This guide will illuminate the path, providing a detailed roadmap for establishing secure connections for your IoT devices using the versatile Raspberry Pi, all while unearthing a treasure trove of free resources to fuel your projects.
Whether you are a seasoned professional or just beginning your journey, this article is designed to empower you. We will delve into step-by-step instructions and insightful guidance, unraveling the intricacies of securing IoT devices. By the conclusion, you'll possess a comprehensive understanding of crafting a secure and resilient environment for your IoT endeavors. This exploration goes beyond theory; its firmly rooted in practical solutions, real-world examples, and expert advice. We will dissect the 'how' and 'why' to ensure your IoT setup is both secure and efficient. The focus will be on providing actionable intelligence. Lets begin the journey, and explore how to achieve a secure connection for your remote IoT devices using a Raspberry Pi, transforming potential vulnerabilities into fortified strengths.
The information provided in this article is for educational purposes only. The author(s) and publisher(s) of this article do not provide any warranty about the content, including its accuracy or usefulness.This article is intended to provide information to the readers, and not to provide any kind of specific advice on technology and internet privacy. Readers should consult with qualified professionals for specific advice.
- Access Iot Devices Remotely For Free Your Ultimate Guide
- Secure Iot Connect Raspberry Pi To Vpc Manage Remotely
Table of Contents
- Introduction to IoT VPC
- Raspberry Pi Setup
- Secure Communication Protocols
- VPC Configuration for IoT
- Remote Access Solutions
- Free Resources for IoT Projects
- Troubleshooting Common Issues
- Best Practices for IoT Security
- Case Studies and Real-World Examples
- Conclusion
Introduction to IoT VPC
A Virtual Private Cloud (VPC) stands as the bedrock of securing IoT devices. It constructs an isolated sanctuary where your IoT devices can communicate securely, shielded from the prying eyes of the public internet. By strategically deploying a VPC, you gain the authority to meticulously control access to your devices, ensuring that only those with proper authorization can interact with them. This level of control is essential in an environment where the integrity of your data and the security of your operations are paramount. The VPC offers a layer of protection that is indispensable in the modern IoT landscape.
Why Use VPC for IoT?
The adoption of a VPC for IoT projects delivers a multitude of advantages:
- Enhanced Security: It isolates devices from the public internet, significantly reducing the attack surface and mitigating potential risks.
- Improved Performance: VPCs frequently contribute to lower latency and more streamlined data transfer, resulting in enhanced responsiveness and efficiency.
- Granular Control: VPCs allow you to exert exacting control over network traffic and access permissions, tailoring your security posture to the specific needs of your IoT ecosystem.
VPCs prove especially invaluable when managing remote IoT devices that engage in frequent data exchanges. They fortify a secure and dependable connection, ensuring that your devices function seamlessly, even in the most demanding environments. The combination of security, performance, and control makes the VPC a critical component for any serious IoT deployment.
- Miaz Vs Girthmaster Adult Product Showdown Amp Comparison
- Free Remote Iot Management Your Guide To Costeffective Solutions
Raspberry Pi Setup
The Raspberry Pi, a versatile and affordable single-board computer, has become a favored instrument for managing and securing IoT devices. Setting up a Raspberry Pi for IoT projects involves a sequence of steps, starting with hardware configuration and progressing to software installation. The Raspberry Pi's adaptability and ease of use make it an ideal platform for both beginners and experienced developers alike. It's the perfect gateway into secure and efficient IoT development.
Steps to Set Up Raspberry Pi
Here’s a quick guide to setting up your Raspberry Pi:
- Install the latest version of Raspberry Pi OS: This is the foundation of your system. Download the OS image from the official Raspberry Pi website and flash it onto your SD card. Ensure you choose the appropriate version for your Pi model.
- Connect your Raspberry Pi: Hook up your Raspberry Pi to a monitor, keyboard, and mouse. This will allow you to interact with the system directly.
- Update the operating system: Once the OS is installed, update the OS with the following commands:
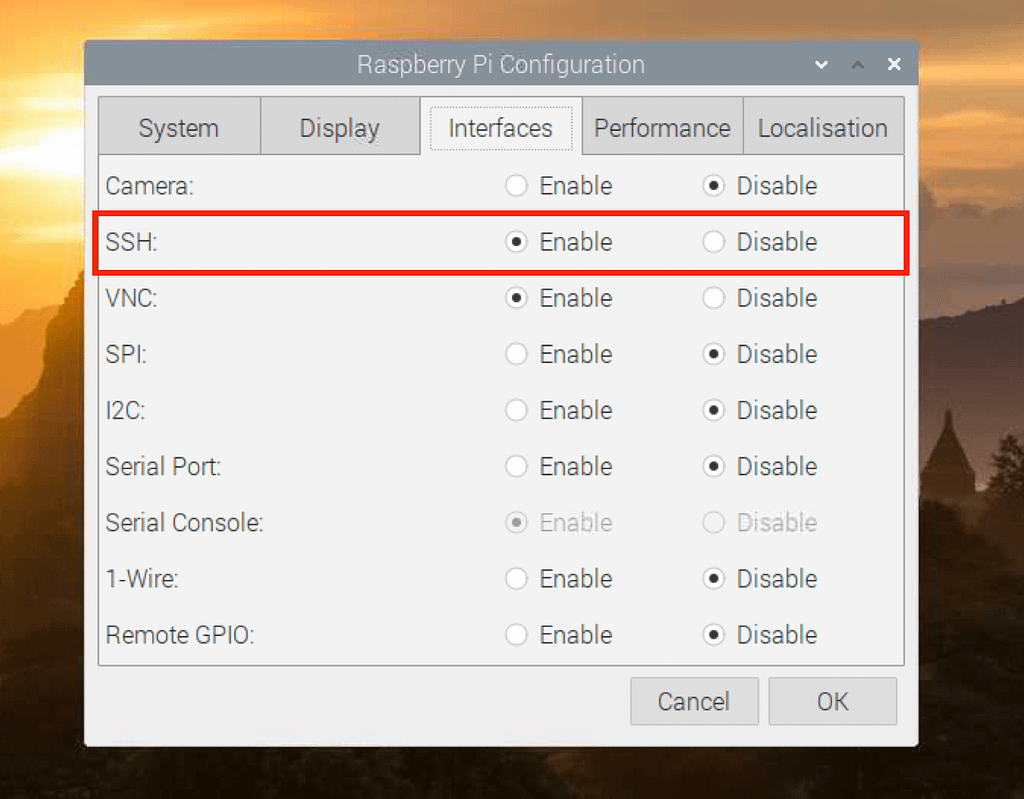
sudo apt update && sudo apt upgrade. This keeps the system updated with all the required packages. - Install SSH and VNC: Install software packages, such as SSH and VNC, for remote access: SSH (Secure Shell) provides a secure way to access the command line remotely, while VNC (Virtual Network Computing) allows you to view and control the Raspberry Pi's graphical desktop.
With your Raspberry Pi now configured, you can transition to the more complex task of setting up IoT applications. This setup guarantees it is well-equipped to interface with your VPC, ready to play its vital role in your secure IoT framework.
Secure Communication Protocols
The security of communication between IoT devices and your VPC is critical to protecting sensitive data. Various protocols can be utilized to achieve this goal, including MQTT, HTTPS, and TLS. The right choice of protocol can make all the difference in your system's security posture. A well-chosen protocol will minimize the risks associated with unauthorized access and data breaches.
Choosing the Right Protocol
Each protocol is designed with its own strengths and weaknesses in mind:
- MQTT (Message Queuing Telemetry Transport): This is a lightweight protocol ideal for low-bandwidth environments. Its efficiency makes it a perfect fit for devices that have limited resources.
- HTTPS (Hypertext Transfer Protocol Secure): HTTPS is a secure web communications protocol. It provides encryption of data transmitted between the device and the server, safeguarding the integrity and confidentiality of communications.
- TLS (Transport Layer Security): TLS provides end-to-end encryption. This protocol ensures that data is encrypted from the origin to the destination, adding an extra layer of security for all types of data transfer.
The ideal protocol will vary depending on the unique needs of your IoT project. Consideration should be given to factors like bandwidth limitations, security requirements, and the nature of data being transmitted. A thorough evaluation is essential before settling on a communication protocol.
VPC Configuration for IoT
Configuring a VPC for IoT involves setting up subnets, security groups, and access control lists, the necessary elements for secure device communication. These elements ensure that the data transfer between devices is secure and protected from potential intrusion. Configuration is the essential step in the process, without which, a VPC will not deliver the security it is designed for.
Key Steps in VPC Configuration
Here are the essential steps to configure your VPC:
- Create a VPC with a unique CIDR block: The CIDR block must be carefully chosen to provide sufficient address space for your devices. The creation of a VPC is the initial step.
- Set up public and private subnets: This helps segregate device traffic. Public subnets can host resources that need to be accessible from the internet, while private subnets keep resources that should not be directly exposed.
- Configure security groups: Security groups determine which traffic is allowed to and from your devices. They act as a virtual firewall.
- Use NAT gateways: NAT gateways allow private devices to access the internet securely. This is useful when devices in the private subnet need to download updates.
By executing these steps, you can forge a robust VPC environment tailor-made for your IoT needs. These actions will ensure that your data is protected. Your system will be robust and ready to meet the challenges of a secure and effective IoT deployment.
Remote Access Solutions
Remote access is essential for managing IoT devices that are deployed in remote locations. Several tools and methods can be used to achieve secure remote access, including SSH, VPN, and cloud-based solutions. The ability to remotely manage your devices is crucial for maintenance, troubleshooting, and the monitoring of IoT devices. The right approach to remote access ensures that you maintain control of your devices, no matter where they are located.
Best Tools for Remote Access
Consider the following tools for secure remote access:
- SSH (Secure Shell): Provides access to your remote devices from a secure command line. SSH uses a strong encryption, allowing for the safe transfer of data.
- VPN (Virtual Private Network): Offers encrypted access to your VPC from virtually any location. By utilizing a VPN, you can create a secure tunnel for all your network traffic.
- Cloud Services: Platforms such as AWS IoT Core offer built-in remote access capabilities. This can simplify the access management process, with various features that are tailored for IoT devices.
Each tool carries its own advantages, so choose the one that best suits your project's requirements. The specifics of your project will drive your choices regarding the best tools. Take time to review each option and pick the best fit.
Free Resources for IoT Projects
A wealth of free resources awaits, ready to enhance your IoT projects. From open-source software to online tutorials, these resources can significantly reduce development expenses while providing valuable insights and knowledge. Taking advantage of these free resources is a smart way to accelerate your learning curve and minimize the cost of your project. There are various resources you can use to get a head start. The opportunities for learning are truly vast, and the available resources are more than enough.
Top Free Resources for IoT
Here are some of the best free resources for IoT:
- Raspberry Pi Documentation: Comprehensive guides and tutorials for setting up and using Raspberry Pi. These resources provide in-depth information.
- MQTT Eclipse: Provides open-source MQTT broker and client tools. These tools are ideal for those who require robust messaging solutions.
- GitHub Repositories: A vast collection of IoT projects and code samples. GitHub offers examples and templates that can serve as springboards for development.
By leveraging these resources, you can accelerate your IoT development and achieve better results. With diligent use of these resources, you will find that your projects develop at a faster pace.
Troubleshooting Common Issues
Despite meticulous planning, issues can arise when setting up and managing IoT devices. Understanding these potential issues, alongside their solutions, will boost your troubleshooting effectiveness. Being prepared to address these issues is critical for ensuring a stable and secure IoT environment. These problems may appear from time to time, but with preparation, you can tackle them.
Common Issues and Solutions
Here are some common issues and their solutions:
- Connection Failures: Verify network settings and make certain that all devices are accurately configured. Take the time to ensure that your network configuration is correct.
- Security Breaches: Regularly update software and utilize robust encryption protocols. Security vulnerabilities can be addressed with regular updates, and you should remain vigilant.
- Performance Issues: Take steps to optimize data transfer and minimize unnecessary traffic. Improving system efficiency involves optimizing the data transfer process and reducing unnecessary traffic.
By addressing these issues promptly, you can maintain a stable and secure IoT environment. The key is to be aware of the potential pitfalls and have a plan ready to implement. Quick action is often the key to a successful resolution.
Best Practices for IoT Security
Implementing the best practices in your IoT devices is essential for ensuring their security. These practices span everything, from device configuration to network management. Prioritizing security is not an option; it is a fundamental necessity for any IoT deployment. These steps are crucial for those who want to build and run a safe IoT system. Follow best practices, and your efforts will be well-placed.
Key Best Practices
Here are some best practices to follow:
- Regularly update firmware and software: Doing this is the only way to defend against any vulnerabilities.
- Utilize strong passwords and multi-factor authentication: Limit unauthorized access and use strong security.
- Monitor network traffic: Look for any suspicious activity, and respond swiftly to potential dangers. Its important to understand what's happening in your network.
Following these practices will help you maintain a secure and reliable IoT infrastructure. By embracing these strategies, youll establish a resilient, secure system.
Case Studies and Real-World Examples
Examining real-world examples can give valuable insights into how to successfully implement secure IoT solutions. These case studies show the challenges and solutions encountered in different industries. Looking at these examples can provide inspiration and guidance. Knowing how others have solved their own problems is extremely valuable.
Case Study
The agriculture industry now uses IoT devices to monitor soil moisture, temperature, and other environmental factors. Securely connecting these devices to a VPC with a Raspberry Pi allows farmers to make data-driven decisions that optimize crop yields. In the agricultural world, technology can transform how crops are grown. A well-designed, secure system helps farmers increase their productivity.
Table with Bio Data, Personal Information, Career and Professional Information
Since the article is on securing remote IoT devices, there is no specific person to create the table for, instead here's a table representing different facets of securing remote IoT devices.
| Category | Details | Relevance to IoT Security | Example |
|---|---|---|---|
| VPC Configuration | Setting up subnets, security groups, and access control lists. | Ensuring secure communication and isolation of IoT devices. | Creating a private subnet for IoT devices and restricting access via security groups. |
| Secure Communication Protocols | Implementing MQTT, HTTPS, and TLS. | Protecting data in transit and maintaining confidentiality. | Using TLS for encrypting data transmitted between sensors and the cloud. |
| Raspberry Pi Setup | Installing OS, updating packages, and enabling remote access. | Setting up a secure gateway for device management. | Configuring SSH access to Raspberry Pi for secure remote control. |
| Authentication and Authorization | Implementing strong passwords, multi-factor authentication, and access controls. | Preventing unauthorized access to devices and data. | Requiring multi-factor authentication for accessing the management console. |
| Regular Updates and Patching | Keeping firmware and software up-to-date. | Mitigating vulnerabilities and ensuring security. | Scheduling regular updates for all IoT devices and the Raspberry Pi. |
| Network Monitoring and Intrusion Detection | Monitoring network traffic for suspicious activity. | Detecting and responding to potential threats. | Implementing a system to monitor network traffic and alert on unusual patterns. |
| Data Encryption | Encrypting data at rest and in transit. | Protecting sensitive data from unauthorized access. | Encrypting the data stored on the IoT devices and using TLS for data transfer. |
| Security Audits and Assessments | Regularly reviewing security configurations and practices. | Identifying and addressing potential security weaknesses. | Conducting periodic vulnerability assessments and penetration testing. |
| Physical Security | Securing devices from physical tampering and unauthorized access. | Protecting devices from being physically compromised. | Ensuring devices are installed in secure locations and protected from tampering. |
| Incident Response Plan | Having a plan for responding to security breaches. | Quickly addressing and mitigating the impact of security incidents. | Defining a detailed incident response plan that includes procedures for containment, eradication, and recovery. |
For further reading on secure IoT practices, you can explore resources from reputable organizations such as the OWASP (Open Web Application Security Project) and NIST (National Institute of Standards and Technology). These sites provide in-depth guides and best practices to follow.
Here is a link to the NIST: NIST Website.
Conclusion
Securing remote IoT devices through a VPC using a Raspberry Pi is a critical step in ensuring the safety and reliability of your IoT projects. This article has provided a comprehensive guide to setting up and managing a secure IoT environment, covering everything from VPC configuration to best practices for security. The process of safeguarding your system should now be clear. The steps outlined in this guide will enable you to create a strong and dependable structure for your IoT ecosystem. Embrace these practices, and you'll be well-positioned to protect your data and devices.
We encourage you to apply the knowledge gained from this article to your own projects and explore the free resources mentioned to enhance your development process. Don’t forget to share your thoughts and experiences in the comments section below, and consider exploring other articles on our site for more insights into the world of IoT.

Detail Author:
- Name : Mr. Glen Keeling III
- Username : abernathy.rafaela
- Email : rmcdermott@mills.com
- Birthdate : 1971-12-27
- Address : 1283 Loyal Viaduct North Wainoburgh, MA 43568-8260
- Phone : 539.268.1689
- Company : Ledner-Howe
- Job : Probation Officers and Correctional Treatment Specialist
- Bio : A fugiat sapiente aliquam voluptatem. At omnis consequuntur sint soluta placeat molestiae eum.
Socials
twitter:
- url : https://twitter.com/rahsaan_id
- username : rahsaan_id
- bio : Et magni laborum et. Quibusdam et dolor animi et sed velit veritatis qui. Harum ullam possimus optio dignissimos reiciendis quia aut temporibus.
- followers : 2699
- following : 2158
facebook:
- url : https://facebook.com/vonrueden2024
- username : vonrueden2024
- bio : Maiores quo eveniet voluptates omnis quia modi nam.
- followers : 1106
- following : 1756
linkedin:
- url : https://linkedin.com/in/rahsaan_dev
- username : rahsaan_dev
- bio : Et autem nihil nihil laudantium eos.
- followers : 6426
- following : 1807
tiktok:
- url : https://tiktok.com/@rahsaan5145
- username : rahsaan5145
- bio : Ab blanditiis et excepturi dicta. Labore ut officiis quisquam voluptas.
- followers : 4952
- following : 316