RemoteIoT, VPC SSH & Raspberry Pi: Secure Remote Access Guide
Are you looking for a way to manage your Internet of Things (IoT) devices remotely, securely, and efficiently? Building a RemoteIoT system with Virtual Private Cloud (VPC) SSH and a Raspberry Pi provides unparalleled control and security for your connected devices.
In an increasingly interconnected world, the ability to access and control devices from anywhere is paramount. This article delves into the practical steps required to build such a system, covering the essential components: RemoteIoT, VPC SSH, Raspberry Pi, and the necessary Windows utilities. It navigates the complexities of setting up a secure network, providing clear instructions suitable for both beginners and seasoned tech enthusiasts. The ultimate goal is to equip you with the knowledge to create a robust and reliable remote IoT infrastructure that can handle the demands of the modern digital landscape. This guide provides detailed insights into each aspect, from initial setup to troubleshooting, ensuring a smooth and successful implementation.
This setup allows you to access your devices from anywhere in the world securely. In this article, we will explore the tools and techniques required to achieve this goal, including downloading free Windows utilities.
- Discover Fry99com Your Ultimate Guide To Online Gaming Adventures
- Remote Iot Behind Firewalls Secure Access Best Practices
By the end of this guide, you'll understand how to configure RemoteIoT, set up VPC SSH, and optimize your Raspberry Pi for remote access.
| Topic | Details |
|---|---|
| RemoteIoT | Enables users to manage IoT devices remotely, offering comprehensive device monitoring, configuration management, and data visualization. |
| VPC SSH | Provides secure and encrypted connections to your devices, crucial for protecting sensitive data transmitted over the network. It offers scalability, allowing your network to grow as your IoT needs evolve. |
| Raspberry Pi | A cost-effective and flexible single-board computer ideal for IoT projects. It offers low power consumption, compatibility with multiple operating systems, and a wide range of peripherals, making it a versatile platform for remote device management. |
| Free Windows Tools | Enhance the RemoteIoT experience through tools like PuTTY (SSH client), WinSCP (secure file transfer), and Visual Studio Code (code editor with IoT support). |
For more information about Raspberry Pi, visit the official Raspberry Pi Foundation website.
The following sections detail the necessary steps, from selecting a cloud provider to implementing the security measures that will safeguard your devices.
- Isabella Jane Cruise The Rising Star Her Journey
- Camilla Arauacutejo Age Facts Controversy Amp Career Insights
RemoteIoT is a powerful solution that enables users to manage IoT devices remotely. By combining it with VPC SSH, you can create a secure and scalable network. The integration of Raspberry Pi further enhances this setup by providing a cost-effective and flexible hardware platform.
Why Choose VPC SSH?
Virtual Private Cloud (VPC) SSH offers several advantages:
- Enhanced Security: Protect your data with encrypted connections.
- Scalability: Easily expand your network as your needs grow.
- Cost-Effective: Utilize cloud services without breaking the bank.
Incorporating these technologies into your workflow can significantly improve efficiency and reliability.
The Raspberry Pi is a versatile single-board computer that has gained immense popularity among hobbyists and professionals alike. Its compact size, affordability, and flexibility make it ideal for IoT projects.
Key Features of Raspberry Pi
- Low power consumption
- Support for multiple operating systems
- Compatibility with a wide range of peripherals
When combined with RemoteIoT and VPC SSH, the Raspberry Pi becomes a powerhouse for remote device management.
Creating a VPC is a crucial step in establishing a secure remote network. Follow these steps to set up your VPC:
Step-by-Step Guide
Choose a cloud provider that supports VPC (e.g., AWS, Google Cloud).
Create a new VPC and define its IP address range.
Set up subnets and configure routing tables.
Enable SSH access by configuring security groups.
By following these steps, you can create a secure and functional VPC for your IoT devices.
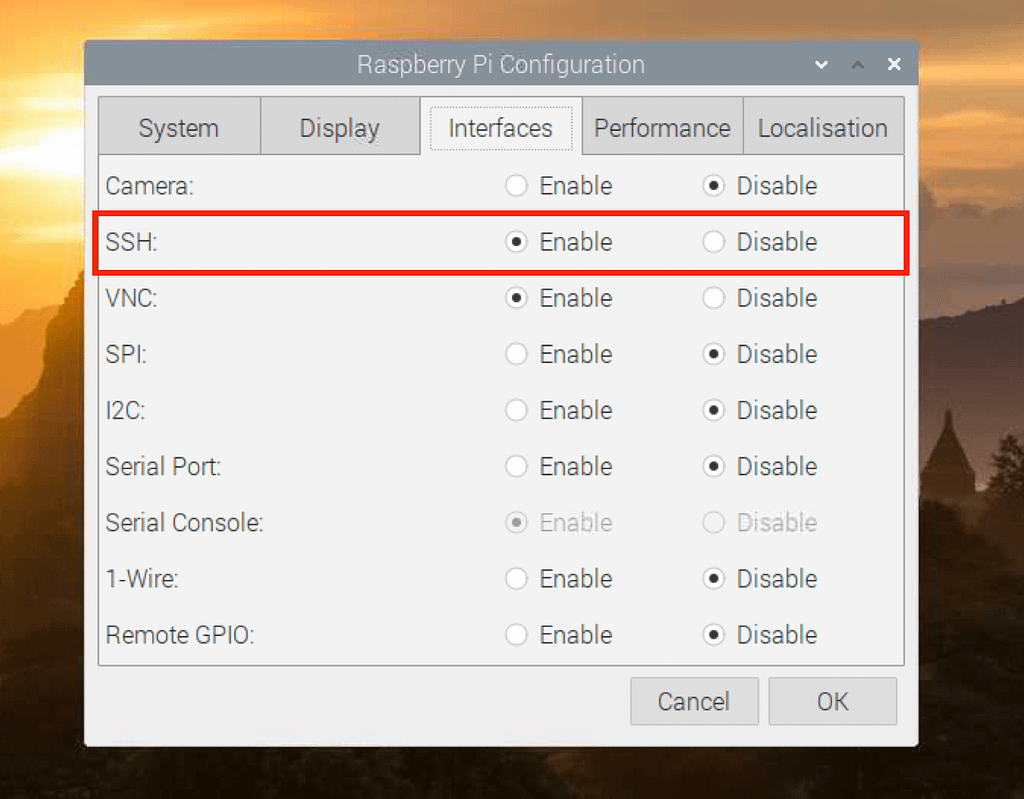
SSH (Secure Shell) is a protocol that allows secure remote access to your Raspberry Pi. Here's how you can enable it:
Enabling SSH
Connect your Raspberry Pi to a monitor and keyboard.
Open the terminal and type the following command:
sudo raspi-config.Navigate to "Interfacing Options" and enable SSH.
Reboot your Raspberry Pi to apply the changes.
Once SSH is enabled, you can access your Raspberry Pi remotely from any device on the same network.
RemoteIoT provides a suite of tools that simplify the management of IoT devices. These tools include:
Popular RemoteIoT Tools
- Device monitoring software
- Configuration management tools
- Data visualization platforms
By leveraging these tools, you can gain better control over your IoT ecosystem and improve overall performance.
There are several free Windows tools available that can enhance your RemoteIoT experience. Some of the most popular ones include:
Recommended Tools
- PuTTY: A free SSH client for Windows.
- WinSCP: A secure file transfer program.
- Visual Studio Code: A versatile code editor with IoT support.
These tools can be downloaded from their official websites, ensuring you receive the latest and most secure versions.
Even with the best setup, issues can arise. Here are some common problems and their solutions:
Problem
- Ensure SSH is enabled on your Raspberry Pi.
- Check your network settings and firewall rules.
- Verify the IP address and port number.
By addressing these issues, you can restore connectivity and maintain a stable remote connection.
Security should always be a top priority when setting up a remote IoT network. Here are some best practices to follow:
Key Security Measures
- Use strong, unique passwords for all devices.
- Enable two-factor authentication whenever possible.
- Regularly update your software and firmware.
Implementing these measures will help protect your network from unauthorized access and potential threats.
To ensure optimal performance of your RemoteIoT setup, consider the following tips:
Optimization Strategies
- Minimize unnecessary services running on your Raspberry Pi.
- Use compression techniques to reduce data transfer overhead.
- Monitor network traffic and adjust settings as needed.
By optimizing your setup, you can achieve faster response times and improved reliability.

Detail Author:
- Name : Miracle Tromp II
- Username : stephanie52
- Email : qwalker@breitenberg.net
- Birthdate : 1991-04-01
- Address : 435 Dominic Mall New Sydneystad, KY 63466
- Phone : 1-858-593-4802
- Company : Keeling, Conroy and Jacobi
- Job : Industrial Engineer
- Bio : At rem rerum commodi recusandae qui aut. At sit voluptas perspiciatis debitis. Sunt consequatur minus velit doloribus animi fugiat consequuntur.
Socials
instagram:
- url : https://instagram.com/murray_keeling
- username : murray_keeling
- bio : Perferendis nemo porro praesentium. Repudiandae non animi quibusdam aliquid accusantium.
- followers : 5743
- following : 436
tiktok:
- url : https://tiktok.com/@murray_keeling
- username : murray_keeling
- bio : Accusamus impedit quas vel numquam aut libero.
- followers : 3285
- following : 1406
twitter:
- url : https://twitter.com/murray.keeling
- username : murray.keeling
- bio : Nobis est eaque voluptates vitae aperiam et voluptatem similique. Commodi occaecati rerum alias repellat consequuntur exercitationem ab qui.
- followers : 1104
- following : 2691